Endoacustica offers, Exclusive Customer Service and free Training
Security & Digital Investigation Services
Integrated protection for places, people and information: TSCM (bug sweep), video surveillance, penetration testing and digital forensics. We design, install and validate against professional standards.
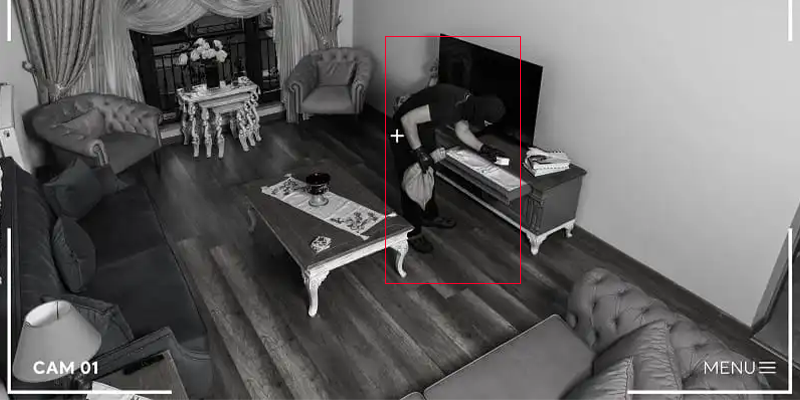
Video Surveillance
HD CCTV/IPC systems with secure remote management (smartphone/PC). Design to code, installation and maintenance on new or existing setups.
- Access control for sensitive areas with event recording.
- Continuous monitoring with time‑and‑place traceability.
- Maintenance, updates and privacy/GDPR adjustments.
Bug Sweep (TSCM)
Technical and instrumental inspections to find RF, wired or hidden surveillance devices. Formal technical report provided.
- RF analysis up to 14 GHz (spectrum, GSM/2G/3G/4G/5G burst).
- Wi‑Fi/Bluetooth, LJD “wand”, endoscopy and thermography.
- Power/data line inspections and conducted‑wave threats; on‑site removal of findings.

Penetration Testing
Controlled attack simulations across Web/Mobile/API, network and Wi‑Fi to surface exploitable weaknesses. Evidence‑based reporting with CVSS severity and a prioritized remediation plan.
- OWASP · PTES/OSSTMM methodologies.
- Planned test windows to avoid disruption.
- Re‑test to verify implemented fixes.

Mobile Data Extraction
Cellebrite UFED and dedicated tooling to recover SMS/chats, media, geodata, histories and deleted content — with full chain of custody.
- Logical, physical, chip‑off and backup extraction (where available).
- Forensic image, event timeline and technical report.
- Expert support for litigation and internal investigations.

Frequently asked questions
What does a TSCM bug sweep include?
How long does a TSCM engagement take and what do you need for a quote?
Will a penetration test impact production?
What deliverables will we receive?
Do you recover data from locked or damaged devices?
Do you operate lawfully and with privacy safeguards?
Have a project or a concern? Talk to us
A 15‑minute call to define scope and give you the fastest, safest path forward.
Go to contact page